Image credit: Jefferson Santos
If you are interested in pivoting into a cybersecurity career, there are a few steps you can take to prepare. First, it is important to understand the basics of computer technology and networks. You should have a good understanding of how computers work, and be familiar with different operating systems and network architectures. You can gain this knowledge through online courses, books, or by taking classes at a local college or university.
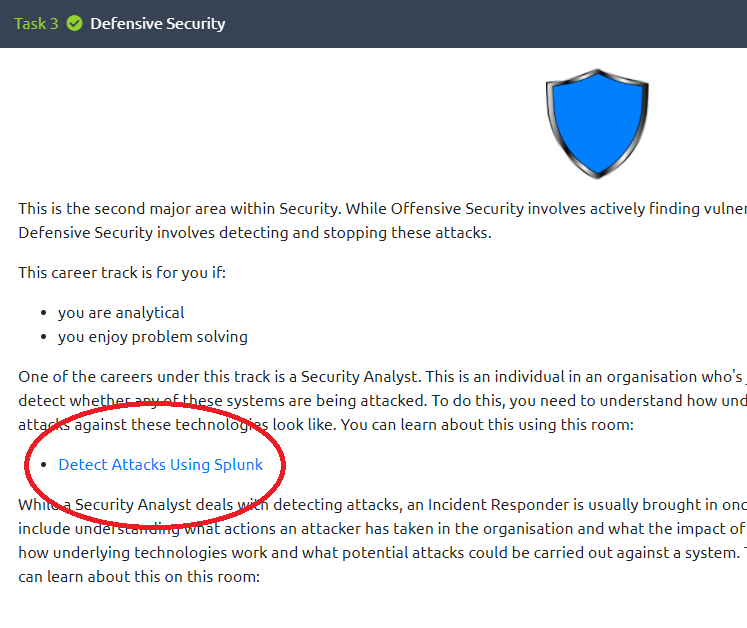
It is also important to gain hands-on experience with cybersecurity tools and technologies. This can be done through internships, part-time jobs, or by participating in online cybersecurity challenges and competitions. These experiences will not only help you learn more about cybersecurity, but they will also help you develop the practical skills and expertise needed to succeed in this field.
In addition to gaining technical knowledge and hands-on experience, it is also important to develop your problem-solving skills. Cybersecurity professionals are often called upon to identify and resolve complex technical issues, so having strong problem-solving skills is essential.
Overall, the key to preparing for a career in cybersecurity is to gain a strong foundation in computer technology and networks, develop hands-on experience with cybersecurity tools and technologies, and hone your problem-solving skills. With dedication and hard work, you can successfully pivot into a career in cybersecurity.
(This article was written by ChatGPT, an Artificial Intelligence chat bot! Learn more about it here!)